It’s a common practice to encrypt the secrets/credentials we use in our code and then save it in some secure place. We have a number of options to achieve this, with tools like Vault, Git-crypt, and more. However, git-secret is one simple awesome tool that we can use to store our secrets in our Git repo. Git secret uses gpg for encryption and decryption of secrets.
Here’s how git-secret works. Go to the folder in your repo in which you have files to encrypt. Then, run git init && git secret init. This would initialize your .gitsecret folder. Then you run git secret tell $email , and if you want other users to decrypt the secrets file you have to import their gpg public key and again run git secret tell $otheruseremailid . Now you can run git secret add $secretfilename and git secret hide,which creates $yoursecretfile.secret file, which is an encrypted secret file.
Now you are good to commit to your master repo. git-secret automatically adds $secretfile to .gitignore so you only commit $secretfile.secret file.
The main challenge in integrating git-secret into Jenkins is that git-secret uses a gpg private key and public key. If we have to run git secret reveal, we should have a gpg private key. So, how do we run this on Jenkins, which uses a slave to pull the repo and build, if you have to reveal git secret in slave you should have gpg private key on your slave. How, do we achieve this encryption and decryption in a Jenkins Pipeline?
These steps will explain using git-secret in Jenkins pipeline.
Running git-secret on Jenkins
1. Export gpg private key.
gpg -a --export-secret-keys $keyid > gpg-secret.key
gpg --export-ownertrust > gpg-ownertrust.txt
You will get a key ID by running gpg --list-secret-keys .
Here E7CD2140FEC5B45F42860B2CC19824F8BC975ABCD is the key ID.
sec rsa4096 2019-09-17 [SC]
E7CD2140FEC5B45F42860B2CC19824F8BC975ABCD
uid [ultimate] Test (test gpg key) <test@domain.com>
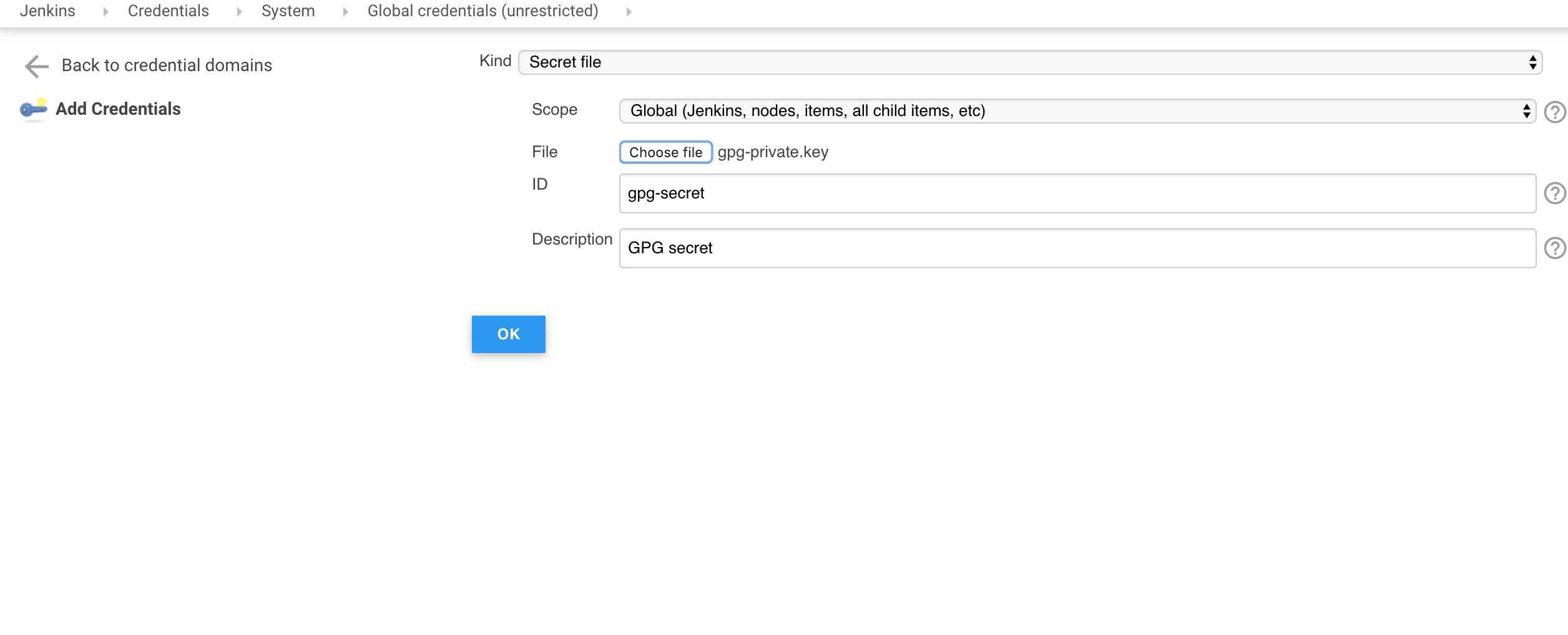
2. Add the exported gpg secret key and owner trust to Jenkins credentials asa a secret file . The below image shows adding a private key as Jenkins credentials. Add the owner trust file in the same way.
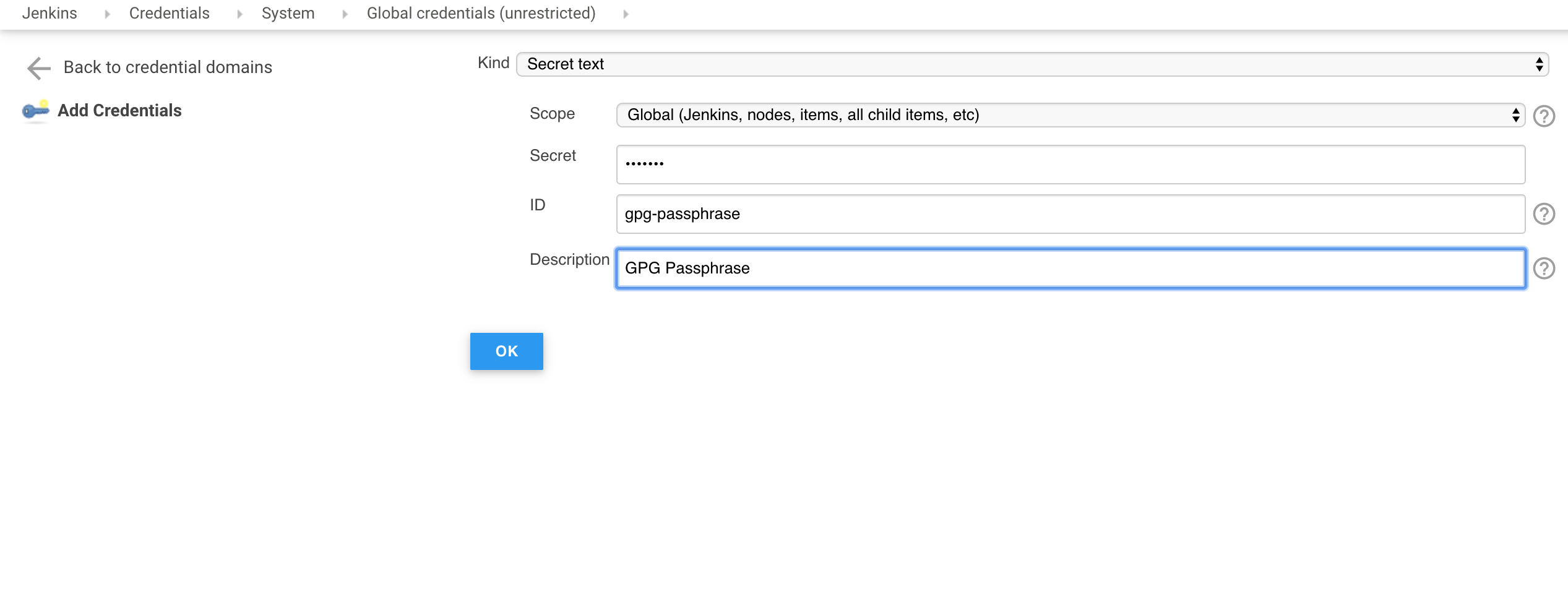
3. Add a passphrase of gpg private key as credentials as a kind secret text . The image below demonstrates this.
4. Use the added gpg private key, owner trust file, and passphrase in the Jenkins Pipeline. Here “gpg-secret,” “gpg-trust,” and “gpg-passphrase” are the IDs given when you add Jenkins credentials.
pipeline {
agent {
node {
label 'test_slave'
}
}
environment {
gpg_secret = credentials("gpg-secret")
gpg_trust = credentials("gpg-trust")
gpg_passphrase = credentials("gpg-passphrase")
}
stages {
stage("Import GPG Keys") {
steps {
sh """
gpg --batch --import $gpg_secret
gpg --import-ownertrust $gpg_trust
"""
}
}
stage("Reveal Git Secrets") {
steps {
sh """
cd $WORKSPACE/$yoursecretfolder
git init
git-secret reveal -p '$gpg_passphrase'
"""
}
}
}
}
I hope this article explains clearly how to use git-secrets in Jenkins Pipeline.